To tag or not to tag…that is the question!
At least it is a question I’m often asked about how the Mikrotik Router treats vlan traffic. In this article, I will address some of the more common types of configurations and help you to understand exactly where you will, or will not, see a packet that is tagged.
Let me begin with the most simple concept, which I hope will lay a good foundation for the remainder of the article. When you create a vlan interface on the Mikrotik, what happens internally is that you sort of “trick” the Mikrotik into thinking that you have added a physical interface. That is not exactly correct, but if you think of it in those terms, the rest of this article will be easier to follow. Consider the following simple network:
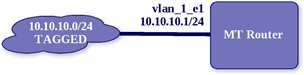
When the MT router needs to communicate with the 10.10.10.0/24 network, it knows that it must send the packet out the interface named “Ether1”. It “learns” that by looking in it’s routing table. It will see that the 10.10.10.0/24 network is “connected” to ether1 based on the IP address assigned to that interface. Let’s look at another simple network diagram:
Similar to the first network, when the MT needs to communicate with the 10.10.10.0/24 network, it looks to it’s routing table. In the above network, the interface with the 10.10.10.1/24 network is a vlan interface named vlan_1_e1. It would be created with the following code:
/interface vlan add name=vlan_1_e1 interface=ether1 vlan-id=1
/ip address add interface=vlan_1_e1 address=10.10.10.1/24
The first line creates a vlan interface with the appropriate name, attaches that vlan to the PHYSICAL interface ether1 and configures the vlan-id (tag) to be “1”. The second line adds an IP address to the vlan interface. Any traffic that is destined for the 10.10.10.0/24 network will leave the router on that interface and, since it is leaving on a vlan interface, this traffic WILL BE TAGGED with vlan-id of 1.
As we continue to examine some further types of configuration possibilities, keep in mind what makes a packet leave the router with (or without) a vlan tag is simply this: anytime a packet leaves the router ON A VLAN INTERFACE, it will be tagged. It is no more complicated that that. Let us consider another network:
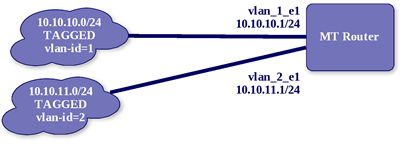
This network works in a way that is very similar to both of the previous network diagrams. Here is the configuration snippet:
/interface vlan
add name=vlan_1_e1 interface=ether1 vlan-id=1
add name=vlan_2_e1 interface=ether1 vlan-id=2
/ip address
add interface=vlan_1_e1 address=10.10.10.1/24
add interface=vlan_2_e1 address=10.10.11.1/24
In this configuration, we have 2 vlans configured on the PHYSICAL ether1 interface. Traffic destined for the 10.10.10.0/24 network will leave on vlan_1_e1 interface and will be tagged with vlan-id of “1”. Likewise, traffic destined for the 10.10.11.0/24 network will leave on the interface named vlan_2_e1 and will be tagged with vlan-id of “2”. If this is not clear, just study the image and configuration and it should become clear. One further note about this configuration is that any device that is connected to the PHYSICAL network off of our ether1 will need to be configured to use the appropriate vlan tag in order to “see” the 10.10.11.1 and 10.10.10.1 IP addresses.
Up to this point, I have been discussing vlans that are used as ROUTED interfaces. Let’s look at a couple of bridged scenarios. Remember that a RouterOS device that has interfaces configured as a bridge is transparent to the network. Take a look at the following configuration snippet:
/interface bridge
add name=bridge1
/interface bridge port
add interface=ether1 bridge=bridge1
add interface=ether2 bridge=bridge1
/ip address
add interface=bridge1 address=10.10.10.1/24
In the above code, we have created a bridge and added interfaces ether1 and ether2 to that bridge. With that configuration, any traffic that enters the router on it’s ether1 port will be passed to the network on it’s ether2 interface UNTOUCHED. What that means is that if traffic is tagged already, then it will still be tagged (in either direction). The IP address that we added is reachable on the network, but ONLY when the packets are UNTAGGED. The router is transparent to the network, but if the network we are plugged into has vlan tags for all traffic, the router will not be reachable on the network. Let’s assume that the network above uses vlan-id=1 for all packets. If we wanted to make the router manageable on that network, we would need to create a vlan interface with the bridge as the master interface as follows:
/interface bridge
add name=bridge1
/interface bridge port
add interface=ether1 bridge=bridge1
add interface=ether2 bridge=bridge1
/interface vlan
add name=vlan_1_b1 interface=bridge1 vlan-id=1
/ip address
add interface=vlan_1_b1 address=10.10.10.1/24
This configuration would cause the router to PASS all traffic untouched through the bridge, but would allow the router to be included in the vlan as well, so that you can manage the router.
Here is another common network scenario:
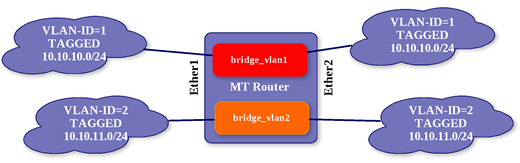
In this situation, you have multiple vlans that must pass through the router. You can accomplish this with the configuration shown above by simply bridging ether1 and ether2, however, there is a more elegant solution if, for some reason, you do not wish to bridge these 2 ethernet ports. Here is the configuration (explanation to follow):
/interface bridge
add name=bridge_vlan1
add name=bridge_vlan2
/interface vlan
add name=vlan_1_e1 interface=ether1 vlan-id=1
add name=vlan_2_e1 interface=ether1 vlan-id=2
add name=vlan_1_e2 interface=ether2 vlan-id=1
add name=vlan_2_e2 interface=ether2 vlan-id=2
/interface bridge port
add interface=vlan_1_e1 bridge=bridge_vlan1
add interface=vlan_1_e2 bridge=bridge_vlan1
add interface=vlan_2_e1 bridge=bridge_vlan2
add interface=vlan_2_e2 bridge=bridge_vlan2
To be honest, although this is a slightly more complex configuration, this is my preferred method when there are multiple vlans that will be passed through the router. The main reason I prefer this type of configuration is because it allows you to view the interface list and see how much traffic is passing on each vlan. A quick inspection of the configuration options shown above will help you understand how it works. First, we create the bridges that will “pass” the traffic for each vlan. The vlan interfaces are then created on each of the physical ethernet ports. By adding these vlan interfaces to a bridge (the last section), we will simply pass traffic WITH TAGS right through the router. This should be clear if you apply the premise I explained early on in this article. That premise being that “anytime a packet leaves the router ON A VLAN INTERFACE, it will be tagged.” Look carefully at the image and the configuration and you should be able to see which interface will be used to carry traffic into and out of the router.
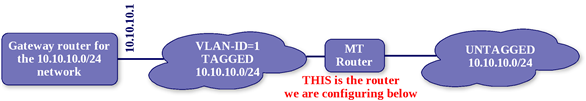
I will offer one final commonly used configuration. Here is the network image:
In this network, we have tagged packets entering the router on ether1 and a network that is untagged on ether2. Devices on the untagged network will NOT be using vlan tags (in fact, they do not even realize there IS a vlan configuration involved). All devices on the left side of the Mikrotik router WILL be using vlan tags. Here is the configuration snippet:
/interface vlan
add name=vlan_1_e1 interface=ether1 vlan-id=1
/interface bridge
add name=bridge1
/interface bridge port
add interface=vlan_1_e1 bridge=bridge1
add interface=ether2 bridge=bridge1
This is a rather simple configuration, but may require some explanation. We first create a vlan interface on ether1, which will be plugged into the TAGGED network. Next, we create a bridge to handle the traffic passing through. The vlan interface is added to the bridge AND the physical ether2 port is added to the bridge. The ether2 port will be plugged into the UNTAGGED network. I will leave it as an exercise for my readers to determine WHY this configuration will cause packets to be either tagged or not tagged as they leave the router.
This is a rather lengthy article and I have covered quite a lot of information. For obvious reasons, I cannot cover 100% of the network configuration possibilities that exist, but I have tried to cover the most commonly used configurations. I hope you find this article helpful and that you will DIGG it (top right). Feel free to add your comments with your special circumstances and how you have solved them. If you need hardware, be sure to drop by my store at http://store.wispgear.net/

November 26th, 2011 at 2:06 pm
Hi Butch,
I have a big problem. Today I tried to test your examples with vlan tag. My scenarios is like this: laptop nic(no vlan capabilities)–>rb750GL–>switch with management vlan 10.
First I create a bridge between 2 ports(ether4 and ether5) then i create a vlan on ether4(management switch) and tried to ping them modem. Laptop and switch are in the same network, but i don’t have any ansver. Can you tel me what I’m doing rong?
Please, I need your help on this!
November 26th, 2011 at 2:48 pm
My bad…. after I submit my first comment, i saw that your final example is what I need. 🙂
November 26th, 2011 at 3:01 pm
I still need your help. In your last example, how can I manage the router from the untag portion of the network?
November 27th, 2011 at 1:28 am
I figured that too, from your examples! Thnak you for your great tutorials!
January 9th, 2012 at 5:31 pm
[…] микротик. Оказа Ñе че това не е най-тривиалната задача и без да Ñе зачета нÑма да […]